Most teams start webhook processing in Node.js with a quick solution: Create an endpoint, parse the payload, and trigger a function.
It works, but as traffic grows and webhook sources increase, the system starts breaking in unexpected ways. The common problem? Hard-coded handlers and brittle logic.
Each new webhook event adds another if/else block. Routing rules are buried inside code.
There’s no configuration layer, & no clean separation between intake and processing. This leads to a fragile webhook architecture in Node.js that becomes risky to maintain.
A SaaS product integrates GitHub, Stripe, and a CRM tool. Each sends different webhook events. The team builds separate handlers inside one Express route.
After a few months, adding a new provider requires code rewrites, redeployments, and regression bugs. One malformed payload crashes the entire webhook pipeline.
- Dynamic routing.
- Rule-based handling.
- Provider-specific validation.
- Retry and queue support.
- Multi-source webhook processing.
Here in this blog, you can see that a configurable webhook processing engine in Node.js becomes important with a structured, scalable way to handle webhook events.
What Is a Configurable Webhook Processing Engine?
A basic webhook listener simply receives HTTP requests and triggers a function.
A Node.js webhook engine goes much further; it receives, validates, routes, transforms, queues, and logs events using configuration instead of hard-coded logic.
Think of it this way:
- Webhook listener → receives data
- Webhook engine → receives + decides + routes + processes
A custom webhook server in Node.js with an engine approach supports:
- Config-driven routing instead of fixed handlers.
- Rule-based processing based on event type and payload.
- Pluggable handler modules.
- Provider-specific validation.
- Processing pipelines.
With configurable webhook routing, you define rules in JSON or a database:
- If source = Stripe → send to billing handler.
- If event = repo.push → trigger CI pipeline.
- If the payload field matches condition → transform and forward.
This creates a multi-source webhook system in Node.js where new integrations don’t require rewriting core logic, just adding new configuration rules.
In short, a webhook system in Node.js becomes a platform capability, not just a route handler.
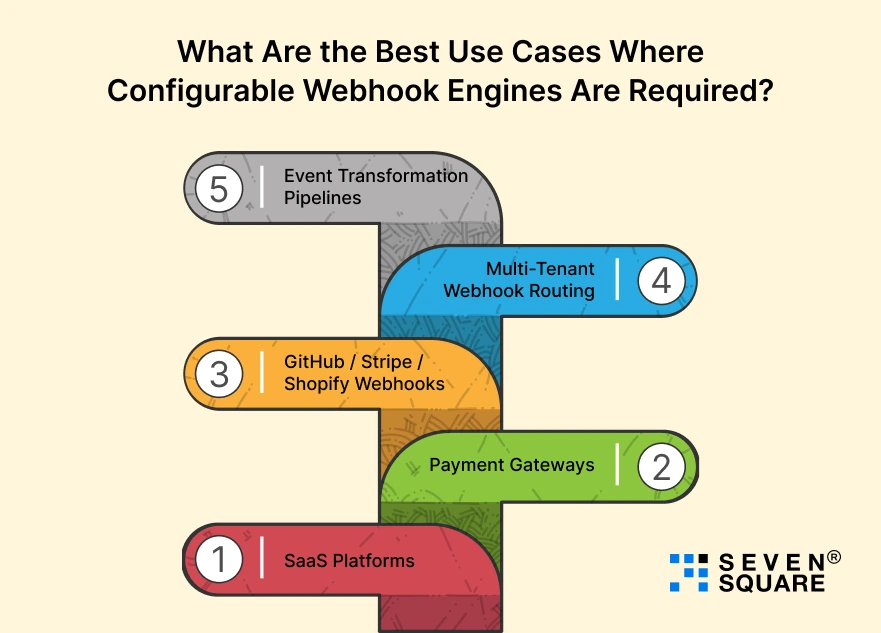
What Are the Best Use Cases Where Configurable Webhook Engines Are Required?
A configurable engine is not over-engineering; it becomes necessary as soon as multiple providers or business rules are involved.
Many real-world systems depend upon structured webhook events in Node.js and real-time webhooks in Node.js to drive automation.
1. SaaS Platforms
- SaaS products receive events from many external systems.
- A webhook engine routes events to the correct module without hard-coded branching logic.
2. Payment Gateways
- Stripe, Razorpay, and PayPal send dozens of event types.
- A rule-based engine processes payment success, refund, and dispute events differently and safely.
3. GitHub / Stripe / Shopify Webhooks
- Each provider has different payload formats and signature rules.
- A configurable Node.js webhook engine supports provider adapters and validation layers.
4. Multi-Tenant Webhook Routing
- In B2B platforms, each tenant may define their own webhook rules.
- A config-driven webhook system routes events based on tenant ID and rules.
5. Event Transformation Pipelines
- Sometimes webhook payloads must be reshaped before forwarding to internal services.
- A processing pipeline transforms data before dispatch, ideal for real-time webhook processing in Node.js.
What Is the Architecture Blueprint for Production-Ready Webhook Engine Design?
A scalable webhook architecture in Node.js should be layered. Each layer has a single responsibility, which improves reliability, testing, and scalability.
This structure supports a scalable webhook processing pipeline instead of a single fragile endpoint.
Request Intake Layer
- Dedicated webhook endpoint.
- Raw body capture.
- Payload size limits.
- Source identification.
Signature Verification Layer
- Provider-specific signature validation.
- HMAC verification.
- Timestamp checks.
- Replay attack protection.
Config Router Layer
- Reads routing rules from config or database.
- Matches event type, headers, and payload fields.
- Selects the correct handler dynamically.
Simple Architecture Diagram
Webhook Request
│
▼
Intake Endpoint (Express/Fastify)
│
▼
Signature Verification
│
▼
Config Router (Rule Engine)
│
▼
Processing Pipeline
│
├──► Queue Worker
│ │
│ ▼
│ Handlers
│
▼
Logs + Storage + Audit
This layered Node.js webhook engine design keeps your webhook processing flexible, secure, and production-ready.
How to Setup the Project of NodeJs Webhook Engine?
A good foundation makes your webhook API Node.js tutorial implementation production-ready from day one.
Express vs Fastify: Which One Should You Use?
Both work well for a webhook endpoint, Express Node.js setup, or Fastify alternative.
Use Express if:
- You want simplicity.
- Large ecosystem & middleware.
- Faster developer onboarding.
- Most webhook examples use Express.
Use Fastify if:
- You need a very high throughput.
- Lower overhead per request.
- Built-in schema validation.
For this webhook engine starter, we’ll use Express because it’s widely used and easier for most teams.
Initialize Project
mkdir nodejs-webhook-engine
cd nodejs-webhook-engine
npm init -y
Install Dependencies
npm install express dotenv crypto body-parser
npm install --save-dev nodemon
Folder Structure of Webhook Engine Design
This structure supports a scalable and configurable webhook system:
nodejs-webhook-engine/
│
├── src/
│ ├── server.js
│ ├── routes/
│ │ └── webhook.route.js
│ │
│ ├── controllers/
│ │ └── webhook.controller.js
│ │
│ ├── services/
│ │ ├── signature.service.js
│ │ └── router.service.js
│ │
│ ├── config/
│ │ └── webhook.config.js
│ │
│ └── utils/
│ └── rawBody.js
│
├── .env
├── package.json
Environment Config
Create .env
PORT=4000
WEBHOOK_SECRET_STRIPE=my_stripe_secret
WEBHOOK_SECRET_GITHUB=my_github_secret
Server Starter File
src/server.js
require('dotenv').config();
const express = require('express');
const webhookRoute = require('./routes/webhook.route');
const app = express();
// raw body required for signature verification
app.use('/webhooks', express.raw({ type: '*/*' }));
app.use('/webhooks', webhookRoute);
app.listen(process.env.PORT, () => {
console.log(`Webhook engine running on port ${process.env.PORT}`);
});
What is the Step-by-Step Guide to Building the Webhook Intake Endpoint?
Now we create the core receive and process webhooks Node.js intake layer.
Create Webhook Route
src/routes/webhook.route.js
const express = require('express');
const router = express.Router();
const controller = require('../controllers/webhook.controller');
router.post('/:source', controller.handleWebhook);
module.exports = router;
This allows:
/webhooks/stripe
/webhooks/github
/webhooks/shopify
Multi-source webhook system is ready.
Webhook Controller
src/controllers/webhook.controller.js
const { verifySignature } = require('../services/signature.service');
exports.handleWebhook = async (req, res) => {
const source = req.params.source;
try {
const rawBody = req.body; // buffer
const headers = req.headers;
console.log(`Incoming webhook from ${source}`);
// verify signature first (security layer)
const isValid = verifySignature(source, rawBody, headers);
if (!isValid) {
return res.status(401).send('Invalid signature');
}
// parse safely AFTER verification
const payload = JSON.parse(rawBody.toString());
console.log("Webhook payload:", payload);
// TODO: send to configurable router engine
// routerService.route(source, payload)
res.status(200).send({ status: "received" });
} catch (err) {
console.error("Webhook processing error:", err.message);
res.status(400).send("Invalid webhook");
}
};
Why Raw Body Handling Matters?
Most providers compute signatures from the raw request body. If you parse JSON before verification → signature breaks → security fails. That’s why we used:
express.raw({ type: '*/*' })
This is critical for webhook security best practices.
Handle Multiple Event Sources
We already support dynamic providers via route param:
/webhooks/:source
This makes your webhook architecture Node.js extensible without new routes.
How to Add Webhook Signature Verification?
Security is not optional in webhook processing Node.js. That’s why webhook signature verification Node.js is mandatory.
Signature Service Module
src/services/signature.service.js
const crypto = require('crypto');
function getSecret(source) {
const map = {
stripe: process.env.WEBHOOK_SECRET_STRIPE,
github: process.env.WEBHOOK_SECRET_GITHUB
};
return map[source];
}
function timingSafeCompare(a, b) {
const buffA = Buffer.from(a);
const buffB = Buffer.from(b);
if (buffA.length !== buffB.length) return false;
return crypto.timingSafeEqual(buffA, buffB);
}
exports.verifySignature = (source, rawBody, headers) => {
const secret = getSecret(source);
if (!secret) return false;
if (source === "stripe") {
return verifyStripe(rawBody, headers['stripe-signature'], secret);
}
if (source === "github") {
return verifyGithub(rawBody, headers['x-hub-signature-256'], secret);
}
return false;
};
HMAC Validation Example: GitHub
function verifyGithub(rawBody, signatureHeader, secret) {
if (!signatureHeader) return false;
const expected = "sha256=" + crypto
.createHmac("sha256", secret)
.update(rawBody)
.digest("hex");
return timingSafeCompare(expected, signatureHeader);
}
HMAC Validation Example: Stripe Style
function verifyStripe(rawBody, header, secret) {
if (!header) return false;
const hash = crypto
.createHmac("sha256", secret)
.update(rawBody)
.digest("hex");
return header.includes(hash);
}
Prevent Replay Attacks
Add timestamp checks (example pattern):
const timestamp = headers['x-signature-timestamp'];
if (Math.abs(Date.now() - timestamp) > 5 * 60 * 1000) {
return false;
}
Prevents attackers from reusing old webhook requests.
Here’s the Complete GitHub Code to Build Configurable Webhook Engine in NodeJs.
What’s Our Node.js Webhook Engine Expertise?
- Our team delivers Node.js webhook engine frameworks that help businesses receive and process webhooks Node.js at scale reliably.
- We build configurable webhook processing Node.js engines with pluggable modules and an extensible webhook handler architecture for SaaS platforms.
- Our custom webhook server Node.js designs support GitHub webhook Node.js, Stripe, and multi-provider webhook system Node.js integrations.
- We optimize webhook processing Node.js performance using scalable webhook processing pipeline patterns & background queue processing strategies.
Want a Customized NodeJs Application for Your Business? Contact Us Now!
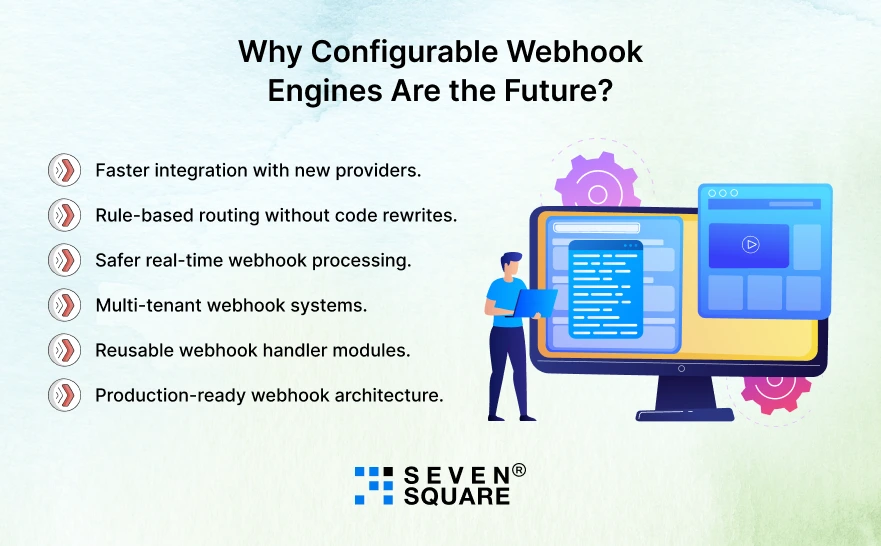
Why Configurable Webhook Engines Are the Future?
Webhook usage is exploding across SaaS, payments, automation, and integrations. But basic listeners are no longer enough.
Teams need a structured webhook architecture in Node.js that supports scale, flexibility, and security.
A configurable webhook processing engine in Node.js gives developers and businesses:
- Faster integration with new providers.
- Rule-based routing without code rewrites.
- Safer real-time webhook processing.
- Multi-tenant webhook systems.
- Reusable webhook handler modules.
- Production-ready webhook architecture.
FAQs
- Webhook processing in Node.js means receiving external event notifications via HTTP and validating, routing, and handling them using server-side logic and processing pipelines.
- You can verify webhook signatures by recreating the provider’s HMAC hash using a shared secret and comparing it with the signature header to ensure authenticity.
- Scale webhook processing using queues, async workers, horizontal scaling, and a scalable webhook processing pipeline with retry support.
- Configurable webhook routing means routing webhook events using rules and configuration instead of hard-coded logic, enabling flexible multi-source webhook systems.