Many ReactJS authentication systems look perfect during development, login works, APIs respond, and tokens are stored, but fail badly in production.
The most common React authentication issues come from small decisions that seem harmless at first:
- Storing JWT tokens in LocalStorage.
- Using long-lived access tokens.
- Not handling token expiry properly.
- Skipping refresh token logic.
- Ignoring multi-tab or session timeout scenarios.
The big mistake? People assume that “it works locally” means “it’s secure in production.” That’s rarely true. In real-world apps, users face:
- Sudden logouts because access tokens expire.
- Broken sessions occur when multiple API calls fail at once.
- Token leaks caused by XSS vulnerabilities.
- Poor UX due to repeated login prompts.
That’s why secure session management in ReactJS has become a core requirement for any scalable application.
What Is Secure Session Management in ReactJS?
ReactJS session management is about keeping users securely logged in while protecting their data.
In traditional apps, the server manages sessions. But React is a Single Page Application (SPA), the frontend handles most of the logic.
There are two common approaches:
State-Based Authentication
- Session stored on the server.
- Works well for traditional apps.
- Hard to scale with SPAs.
Token-Based Authentication (Most Common)
- Server issues tokens after login.
- React sends tokens with each API request.
- No server-side session storage required.
This is why most modern React apps use JWT authentication in ReactJS.
To balance security and user experience, React apps rely on:
- Short-lived access tokens (for API requests).
- Refresh tokens (to silently renew sessions).
This setup allows apps to stay secure without forcing users to log in again and again.
Access Token vs Refresh Token: What’s the Real Difference?
| Feature | Access Token | Refresh Token |
| Purpose | Used to access protected APIs | Used to get a new access token |
| Usage Frequency | Sent with every API request | Used only when the access token expires |
| Expiration Time | Short-lived (5–15 minutes) | Long-lived (7–30 days) |
| Security Risk if Leaked | Lower (expires quickly) | Higher (must be protected carefully) |
| Storage Location in ReactJS | Memory / state (recommended) | HttpOnly cookies (recommended) |
| Exposed to JavaScript? | Yes (in memory) | No (HttpOnly) |
| Part of Token Refresh Flow | No | Yes |
What Is the Secure Token Flow Architecture? (How Does It Works End-to-End?)
See how a secure JWT token flow is used by production React apps.
Step-by-Step Refresh Token Flow in React
- User Login: User submits credentials → backend validates them.
- Access Token Issued (Short Expiry): Backend returns an access token (valid for a few minutes).
- Refresh Token Stored Securely: The refresh token is stored using HttpOnly cookies.
- API Request Flow: React sends the access token with each request.
- Automatic Token Refresh: When the access token expires: Request fails, the refresh token is used, a new access token is issued, & Original request is retried
- Logout & Token Invalidation: The refresh token is revoked, and the session ends.
Login → Access Token → API Calls → Token Expired → Refresh Token → New Access Token → Continue
This flow ensures secure session management in ReactJS without hurting UX.
How to Implement Secure Session Management in ReactJS? (Step-by-Step)
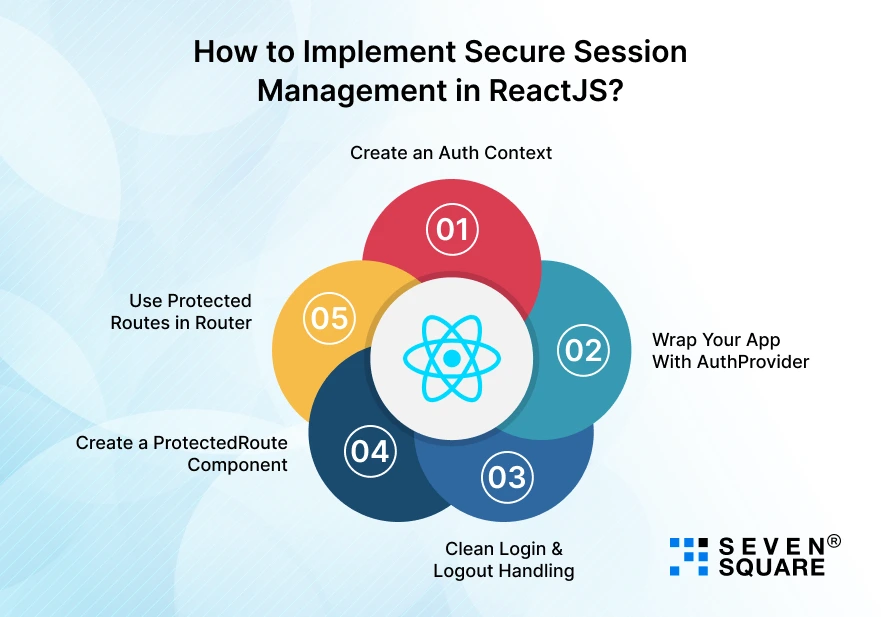
Here you can see how real React apps manage sessions securely.
Setting Up Authentication State in React
To implement secure session management in ReactJS, you need a central place to manage authentication state. The best approach is React Context.
Step 1: Create an Auth Context
src/context/AuthContext.js
import { createContext, useContext, useEffect, useState } from "react";
import axios from "../services/api";
const AuthContext = createContext(null);
export const AuthProvider = ({ children }) => {
const [user, setUser] = useState(null);
const [loading, setLoading] = useState(true);
// Check session on app load
useEffect(() => {
const checkSession = async () => {
try {
const res = await axios.get("/auth/me");
setUser(res.data.user);
} catch (error) {
setUser(null);
} finally {
setLoading(false);
}
};
checkSession();
}, []);
const login = async (email, password) => {
const res = await axios.post("/auth/login", { email, password });
setUser(res.data.user);
};
const logout = async () => {
await axios.post("/auth/logout");
setUser(null);
};
return (
<AuthContext.Provider value={{ user, login, logout, loading }}>
{children}
</AuthContext.Provider>
);
};
export const useAuth = () => useContext(AuthContext);
Why Does This Matter?
- Keeps auth logic centralized.
- Avoids prop drilling.
- Works perfectly with token refresh logic.
- Scales well for SaaS and enterprise apps.
This is the foundation of React secure session management.
Step 2: Wrap Your App With AuthProvider
src/main.jsx or index.js
import React from "react";
import ReactDOM from "react-dom/client";
import App from "./App";
import { AuthProvider } from "./context/AuthContext";
ReactDOM.createRoot(document.getElementById("root")).render(
<AuthProvider>
<App />
</AuthProvider>
);
Step 3: Clean Login & Logout Handling
src/pages/Login.jsx
import { useState } from "react";
import { useAuth } from "../context/AuthContext";
const Login = () => {
const { login } = useAuth();
const [email, setEmail] = useState("");
const [password, setPassword] = useState("");
const handleSubmit = async (e) => {
e.preventDefault();
await login(email, password);
};
return (
<form onSubmit={handleSubmit}>
<input value={email} onChange={(e) => setEmail(e.target.value)} />
<input
type="password"
value={password}
onChange={(e) => setPassword(e.target.value)}
/>
<button type="submit">Login</button>
</form>
);
};
export default Login;
Tokens are not stored manually here; they’re handled securely by backend + cookies.
Protecting Routes in ReactJS
Protected routes are critical for React authentication systems.
Step 4: Create a ProtectedRoute Component
src/components/ProtectedRoute.jsx
import { Navigate } from "react-router-dom";
import { useAuth } from "../context/AuthContext";
const ProtectedRoute = ({ children }) => {
const { user, loading } = useAuth();
if (loading) return <p>Loading...</p>;
if (!user) {
return <Navigate to="/login" replace />;
}
return children;
};
export default ProtectedRoute;
Step 5: Use Protected Routes in Router
src/App.jsx
import { BrowserRouter, Routes, Route } from "react-router-dom";
import Login from "./pages/Login";
import Dashboard from "./pages/Dashboard";
import ProtectedRoute from "./components/ProtectedRoute";
function App() {
return (
<BrowserRouter>
<Routes>
<Route path="/login" element={<Login />} />
<Route
path="/dashboard"
element={
<ProtectedRoute>
<Dashboard />
</ProtectedRoute>
}
/>
</Routes>
</BrowserRouter>
);
}
export default App;
Result
- Unauthenticated users are redirected.
- Authenticated users stay logged in.
- Perfect for protected routes, React authentication.
How to Implement Automatic Token Refresh in ReactJS?
Now let’s implement token refresh React with code using Axios interceptors.
Step 1: Create Axios Instance
src/services/api.js
import axios from "axios";
const api = axios.create({
baseURL: "https://api.example.com",
withCredentials: true, // Required for HttpOnly cookies
});
export default api;
Step 2: Add Response Interceptor for Token Refresh
src/services/api.js
let isRefreshing = false;
let failedQueue = [];
const processQueue = (error, token = null) => {
failedQueue.forEach((prom) => {
if (error) {
prom.reject(error);
} else {
prom.resolve(token);
}
});
failedQueue = [];
};
api.interceptors.response.use(
(response) => response,
async (error) => {
const originalRequest = error.config;
if (
error.response?.status === 401 &&
!originalRequest._retry
) {
if (isRefreshing) {
return new Promise((resolve, reject) => {
failedQueue.push({ resolve, reject });
}).then(() => api(originalRequest));
}
originalRequest._retry = true;
isRefreshing = true;
try {
await api.post("/auth/refresh-token");
processQueue(null);
return api(originalRequest);
} catch (refreshError) {
processQueue(refreshError, null);
window.location.href = "/login";
return Promise.reject(refreshError);
} finally {
isRefreshing = false;
}
}
return Promise.reject(error);
}
);
This is a production-grade Axios interceptors token refresh implementation.
Here’s the Complete GitHub Code to Implement Secure Session Management & Token Refresh in ReactJs.
What’s Our Approach for Secure Session Management & Token Refresh in ReactJs?
- We analyze existing React authentication issues before designing secure session management and refresh token architecture.
- Our team implements short-lived access tokens with automatic token refresh to reduce security risks and improve application stability.
- We ensure protected routes in React authentication are reliable, scalable, and easy to maintain across large applications.
- We build token refresh flows in ReactJS that handle edge cases like multiple failed requests and expired refresh tokens safely.
Want a Custom ReactJs Solution? Contact Us Now!
Building Production-Ready Authentication in ReactJS
Secure session management is non-negotiable for modern React applications. A well-designed setup:
- Protects users.
- Improves retention.
- Scales with SaaS and enterprise needs.
- Prevents costly security breaches.
As your app grows, consider moving more authentication logic to backend services while keeping React lightweight and secure.
With the right approach, secure session management & token refresh in ReactJS becomes a strength.
FAQs
- Yes, when implemented correctly with short-lived access tokens, refresh tokens, and secure storage.
- Yes, they improve UX and reduce security risks caused by long-lived tokens.
- Not suggested. LocalStorage is vulnerable to XSS attacks and token theft.
- Yes. Axios interceptors are widely used for handling automatic token refresh in React safely and cleanly.