Do you know that more than 43% of data breaches involve mobile apps?
That means almost half of all digital attacks come from something users trust most, their smartphones.
Your app isn’t just a product; it’s your brand’s online presence.
But behind that design and smooth UX may lie serious mobile app security risks, from data leaks & insecure APIs to reverse engineering and unauthorized code tampering.
We’ve seen many businesses unknowingly launch apps with weak security layers, only to face performance issues, data exposure, or even financial loss later.
Ensure mobile app security isn’t optional anymore; it’s the backbone of your reputation, user trust, and business growth.
That’s why we believe in secure mobile app development from day one as an integral part of the process.
So if you are trying to learn about mobile application vulnerabilities, then this blog is for you. You will learn about mobile app security best practices to make it secure.
Why Mobile App Security Matters More Than Ever?
Cyberattacks on mobile platforms are increasing every year.
- Hackers are getting smarter, targeting both Android and iOS apps with advanced tools that exploit enterprise mobile app security vulnerabilities.
- Startups and enterprises can no longer afford to treat mobile app data protection lightly.
- A single weak spot could expose sensitive customer data or cause permanent brand damage.
- We help businesses understand that mobile app security best practices are strategic shields protecting your customer trust, compliance (GDPR, HIPAA), and market reputation.
If your app handles personal information, payments, or internal data, security must come before scaling.
Explore the Comparison of Mobile-First vs Mobile-Only.
What Are the Top 10 Mobile App Vulnerabilities You Can’t Ignore?

Even the most innovative mobile apps can be brought down by a single security flaw.
We’ve audited hundreds of applications and found that most security breaches happen because of a few common mobile application vulnerabilities that developers often overlook.
Here are the top 10 mobile app security vulnerabilities every business and developer must fix before launch:
1. Insecure Data Storage
- Cause: Storing sensitive user information (like passwords, tokens, or payment details) directly on the device without encryption.
- Risk: If the device is lost or hacked, attackers can easily access private data.
- Fix: Always encrypt local data using strong algorithms and avoid storing unnecessary personal information.
- Pro Tip: Use encrypted databases like SQLCipher and apply strict access controls.
2. Weak Authentication & Authorization
- Cause: Poorly implemented login systems or missing session checks.
- Risk: Hackers can impersonate users or gain admin access through brute-force attacks.
- Fix: Implement multi-factor authentication (MFA), token-based sessions, and strict password policies.
- Pro Tip: Our mobile app security checklist always starts with securing authentication first because that’s your app’s first line of defense.
3. Unencrypted Data Transmission
- Cause: Sending data over unsecured connections (HTTP instead of HTTPS).
- Risk: Exposes sensitive information during transmission that allows man-in-the-middle attacks.
- Fix: Always use HTTPS/TLS encryption for all communications between app and server.
- Pro Tip: We ensure every app we build follows modern encryption standards and SSL pinning.
4. Poor Session Management
- Cause: Not expiring sessions properly or using weak tokens.
- Risk: Attackers can hijack active sessions and access user accounts.
- Fix: Use secure session IDs, set expiration timeouts, and validate session tokens on every request.
- Pro Tip: We implement session validation as part of our routine app security vulnerabilities testing.
5. Insecure APIs
- Cause: Exposed, unprotected, or poorly designed APIs connecting your app to the backend.
- Risk: Attackers can exploit API endpoints to steal, modify, or delete sensitive data.
- Fix: Use authentication tokens (OAuth 2.0), validate inputs, and encrypt API responses.
- Pro Tip: Our developers run API vulnerability scans for every project to ensure zero backend leaks.
6. Code Tampering & Reverse Engineering
- Cause: Hackers decompile your app’s APK or IPA files to analyze and modify the source code.
- Risk: Leads to data theft, malware injection, or cloning of your app.
- Fix: Use code obfuscation, integrity checks, and runtime verification tools.
- Pro Tip: Our security experts ensure each app undergoes code obfuscation and signature verification before deployment.
7. Inadequate Cryptography
- Cause: Using outdated encryption methods (like MD5 or SHA-1) or weak cryptographic keys.
- Risk: Makes it easy for hackers to decrypt stored or transmitted data.
- Fix: Use modern encryption standards (AES-256, SHA-256) and proper key management systems.
- Pro Tip: We constantly update our cryptography practices as per the OWASP Mobile Top 10 guidelines.
8. Insufficient App Permissions
- Cause: Apps requesting more permissions than they actually need.
- Risk: Increases exposure; a malicious app could misuse camera, mic, or storage access.
- Fix: Follow the principle of least privilege, request only essential permissions.
- Pro Tip: We include permission auditing in our mobile app security checklist for every project.
9. Client-Side Injection
- Cause: Unsanitized input fields or lack of validation in user forms.
- Risk: Hackers inject malicious scripts or SQL commands to manipulate your app’s behavior.
- Fix: Validate all user inputs, use parameterized queries, and sanitize data properly.
- Pro Tip: We apply strict client-side validation and API filtering to eliminate injection flaws.
10. Improper Platform Usage
- Cause: Ignoring platform-specific security practices (like Android Keystore or iOS Keychain).
- Risk: Misuse of platform features can lead to data leaks or insecure configurations.
- Fix: Always follow OS guidelines, use official SDKs, and implement native security features.
- Pro Tip: Our development team uses secure SDK integrations and conducts platform compliance checks for every app we deliver.
Most app security vulnerabilities can be avoided with proper testing, encryption, and validation.
A proactive approach, like following a mobile app security checklist, can save businesses from data breaches, user distrust, and financial loss.
Learn about the Biggest Challenges in Mobile App Development.
How to Prevent These Mobile App Security Issues?
So, how do you keep your mobile app safe from hackers and vulnerabilities?
Here are a few proven ways to prevent mobile app security issues, trusted by our security team:
- Encrypt everything: Use strong cryptographic algorithms to protect stored and transmitted data.
- Secure your APIs: Always authenticate and validate APIs to prevent unauthorized access.
- Perform regular audits: Security audits help identify risks before attackers do.
- Implement strong authentication: Use multi-factor authentication and secure session management.
- Follow the OWASP Mobile Top 10 framework: It’s the global standard for preventing mobile app security vulnerabilities.
We integrate mobile app security best practices into every stage of secure mobile app development, from architecture planning to post-launch monitoring.
Your app deserves more than functionality; it deserves protection from day one.
What is the Mobile App Security Checklist for Businesses?
Before launching your app, you should go through this mobile app security checklist for enterprises:
- Run security audits regularly.
- Encrypt all sensitive data.
- Use HTTPS/TLS protocols for data transfer.
- Perform penetration testing before release.
- Secure backend APIs and database access.
- Apply code obfuscation to prevent reverse engineering.
- Review third-party SDKs and libraries.
- Keep your app dependencies updated.
How Do We Build Security Into Every Mobile App?
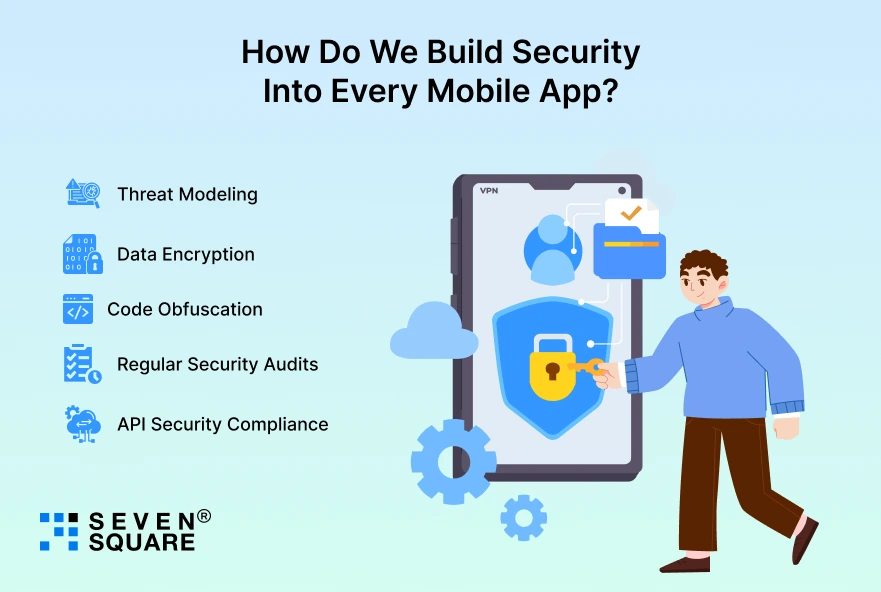
We follow a security-first app development process designed to protect user data and business operations:
- Threat Modeling: Identify potential attack points before development begins.
- Data Encryption: Use advanced cryptographic standards to safeguard information.
- Code Obfuscation: Make app code unreadable to attackers and prevent tampering.
- Regular Security Audits: Continuous testing and updates to eliminate new risks.
- API Security Compliance: Implement strict access controls and authentication mechanisms.
Want Secure Mobile App Development Services? Contact Us Today!
What is the Future of Mobile App Security?
The future of mobile app security is smarter, faster, and more automated. Here’s what’s changing the future of app security:
- AI-based threat detection: Identifies patterns and blocks attacks in real time.
- Biometric authentication: Fingerprints and facial recognition are replacing passwords everywhere.
- Blockchain-based security: Ensures data transparency and tamper-proof storage.
- Cloud-native app protection: Integrated cloud-level encryption and monitoring.
We continuously upgrade our mobile app threat modeling and security solutions to match these trends to ensure our clients stay ahead of evolving threats.
Security is Your App’s Reputation
The top 10 mobile app vulnerabilities can quietly destroy user trust, brand reputation, and even business continuity.
Every unsecured API, weak password, or outdated library opens the door for exploitation.
We believe mobile app security is about building apps that users can truly trust.
Remember:
Secure code + Regular audits + Strong encryption = Long-term business success.
FAQs
- Some of the biggest risks include insecure APIs, poor encryption, data leaks, and reverse engineering.
- Encryption protects sensitive information from unauthorized access during storage and transfer.
- Use a mobile app vulnerability audit checklist, including encryption, API security, and code review.
- Avoid storing sensitive data locally, use HTTPS, and encrypt everything.